Cloud Security Posture Management vs Database Security Posture Management (CSPM vs DbSPM)
Introduction
Just a few years ago, we believed that Cloud Security Posture Management (CSPM) would provide the ultimate security to cloud environments. However, we are now discovering that while CSPM does a good job of identifying infrastructure vulnerabilities, database misconfigurations remain a regular occurrence for cloud-first organizations. This is where Database Security Posture Management (DbSPM) comes into play.
In this blog post, let’s understand the real differences between CSPM and DbSPM to see how each of them play a unique role in securing our digital assets.
Comparative Analysis
| Comparison Parameters | CSPM | DbSPM |
|---|---|---|
| Focus | Securing cloud infrastructures (IaaS, PaaS, SaaS). | Securing databases on cloud and on premises. |
| Scope |
1. Identify misconfigurations, vulnerabilities, and compliance violations in cloud infrastructure. Examples: 2. Categorize the risks based on severity |
1. Identifying misconfigurations, vulnerabilities, and compliance violations in databases. Examples: 2. Categorize the risks based on severity |
| Governance Features | Activity monitoring, resource inventory, alert management, remediation guidance | Activity monitoring, object inventory, alert management, remediation guidance |
| Application | For cloud-first organizations with cloud reliance. | For organizations managing databases with sensitive data. |
| Security Controls |
Cloud infrastructure-related security controls, such as compute and network configurations, access controls, encryption settings, logging and monitoring within the cloud environment. Examples: |
Database-centric security controls, including authentication, authorization and access controls, data encryption, and auditing mechanisms to protect the confidentiality and integrity of data stored in databases. Examples: |
| Asset Inventory | Provides comprehensive visibility into cloud resources and configurations across multi-cloud environments helping organizations maintain a unified view of their cloud assets. | Provides comprehensive visibility into database assets, such as tables, schemas, stored procedures, and indexes, enabling organizations to monitor and manage their database resources. |
| Compliance Monitoring | Ensures adherence to cloud security best practices and compliance frameworks, helping organizations meet industry-specific regulations related to cloud security. | Focuses on ensuring compliance with data protection regulations, such as GDPR, HIPAA, or PCI DSS, and so on by enforcing security policies and monitoring access to sensitive data. |
| Use Cases | 1. Security and Compliance Monitoring of cloud infrastructure: a. Preventing misconfigurations and vulnerabilities in cloud environments b. Minimizing the risk of data breaches and unauthorized access to cloud resources 2. Cloud governance 3. DevSecOps Integration |
1. Security and Compliance Monitoring of databases: |
Banyan Cloud CSPM: What it Offers
Banyan Cloud CSPM detects misconfigurations and vulnerabilities across your cloud infrastructure, categorizes them based on CIA-triad focused risk factors, displays the security posture on a consolidated dashboard, and provides remediation guidance to combat these risks. Additionally, it offers cloud governance capabilities, including resource inventory management, activity monitoring, continuous compliance monitoring, network log management, change inventory, version history and alert notifications.
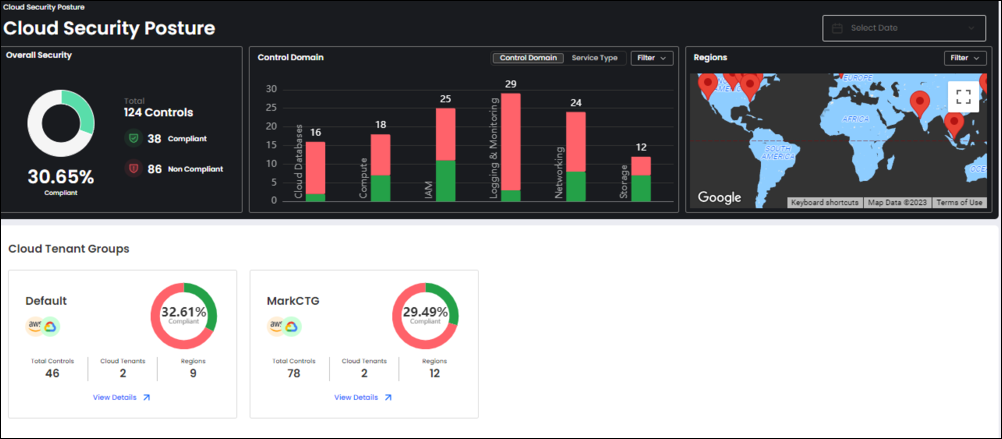
Banyan Cloud DbSPM: What it Offers
Banyan Cloud DbSPM detects misconfigurations and vulnerabilities in databases (residing on both cloud and on-premises), categorizes them based on CIA-triad focused risk factors, displays the security posture on a consolidated dashboard, and provides remediation guidance to combat these risks. Additionally, it offers database governance capabilities, including object inventory, activity monitoring, continuous compliance monitoring, manual validation, change inventory, version history and alert notifications.
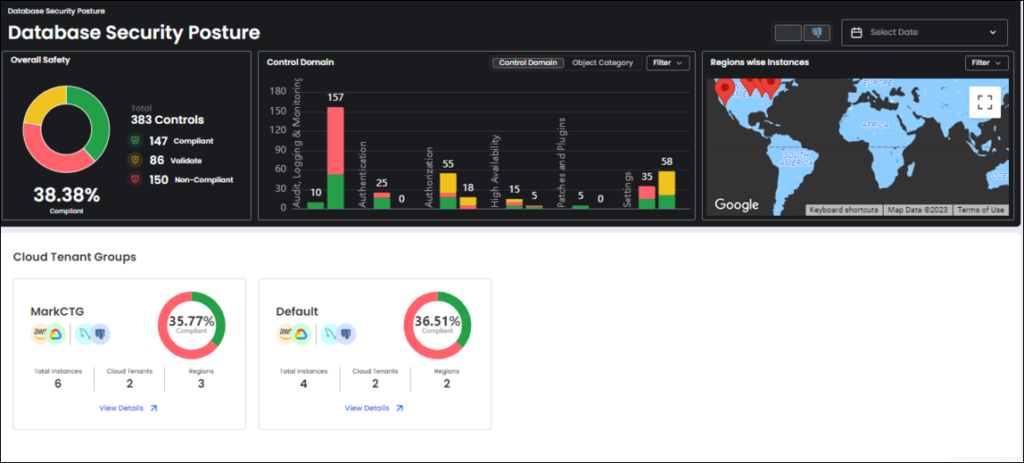
Why Banyan Cloud for Cloud and Database Security & Governance
Banyan Cloud stands as the pinnacle of Cloud Native Application Protection Platforms (CNAPP), seamlessly safeguarding code to cloud. Some of the unique features of Banyan Cloud CNAPP are:
-
- A single SaaS platform with easy onboarding for both cloud and database security posture management and governance
-
- Real-time security monitoring
-
- Fine-grained RBAC providing seven layers of access controls across resources, locations, and so on
-
- CIA-triad based risk factor categorization
-
- Advanced governance features for cloud and databases
-
- Just in Time Download of Security and Compliance Reports
Conclusion
Through our comparison of CSPM and DbSPM, we have recognized their distinct scopes, application areas, and security controls. While CSPM focuses on cloud infrastructures and compliance, DbSPM prioritizes data-centric security measures and database governance. Both play vital roles in safeguarding digital assets, and organizations should consider implementing both solutions for comprehensive security coverage.
Banyan Cloud CSPM and DbSPM offer robust features to address misconfigurations, vulnerabilities, and risk factors. From detecting and categorizing threats to providing remediation guidance, continuous compliance monitoring, and alert notifications, these solutions provide a powerful defense against potential data breaches. Get to know our products better, book a demo today.
